Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
By: Fergal Glynn
The cybersecurity journey for Microsoft has been a long and bumpy one. It began in July 2001 when the Code Red worm targeted Windows-based systems with Microsoft IIS (Internet Information Services for Windows Server) installed. Researchers at eEye Security originally detected Code Red, but the early detection couldn’t stop the spread as more than 300,000 servers globally running Microsoft IIS were attacked.
While this event catalyzed a cybersecurity focus for Microsoft, similar incidents still occur today, with most targeting zero-day vulnerabilities in Microsoft code. For example, in 2017, the WannaCry ransomware attack was a worldwide cyberattack that targeted computers running the Microsoft Windows operating system. In 2022, a series of vulnerabilities in the Microsoft Exchange mail server affected more than 30,000 organizations worldwide (source).
 |
Given its history, Microsoft takes cybersecurity more seriously today. They now offer a complete security stack, with some products integrated into their current offerings (i.e., data classification for Microsoft Office 365) and add-on products for other security categories, all conveniently bundled into their top-tier E5 license. Chief Financial Officers (CFO) around the world, at the prompting of Microsoft direct sellers and an extensive network of channel partners, are compelling Chief Security Officers (CSO) and Chief Information Security Officers (CISO) to get rid of already installed and often high performing cybersecurity solutions from leaders in their categories (i.e., CrowdStrike) in favor of exclusively implementing Microsoft solutions up and down their security stack.
With its far-reaching presence in the corporate world and expansive partner network, Microsoft exerts significant influence on non-security executives, including CEOs, CIOs, CFOs and, in some cases, the Board of Directors. They often tout one thing (and one thing only) in their argument to move their organizations to a full Microsoft security stack - cost saving. For current E5 license holders, it can appear as a compelling financial argument.
I wrote this particular blog post to assist security leaders to parse through Microsoft's Insider Risk and Data Protection offerings and how to effectively navigate the pressures from non-security-focused peers and executives to adopt Microsoft as the single source of security technology.
At Next DLP, we have heard of cases where CISOs are told to deploy Microsoft Purview without ever having been involved in the purchase decision or testing the solution to determine if it best fits their organization’s needs.
Formerly known as Microsoft Information Protection, or MIP for short, Microsoft’s data security solution, Purview, is included in many E5 license tiers. Purview is a collection of different technologies, some developed in-house by Microsoft and others acquired, that have been loosely integrated and rebranded Microsoft Purview. As with any security technology-related decision, there are pros and cons that every CSO or CISO should consider when evaluating whether Purview is right for their organization.
 |
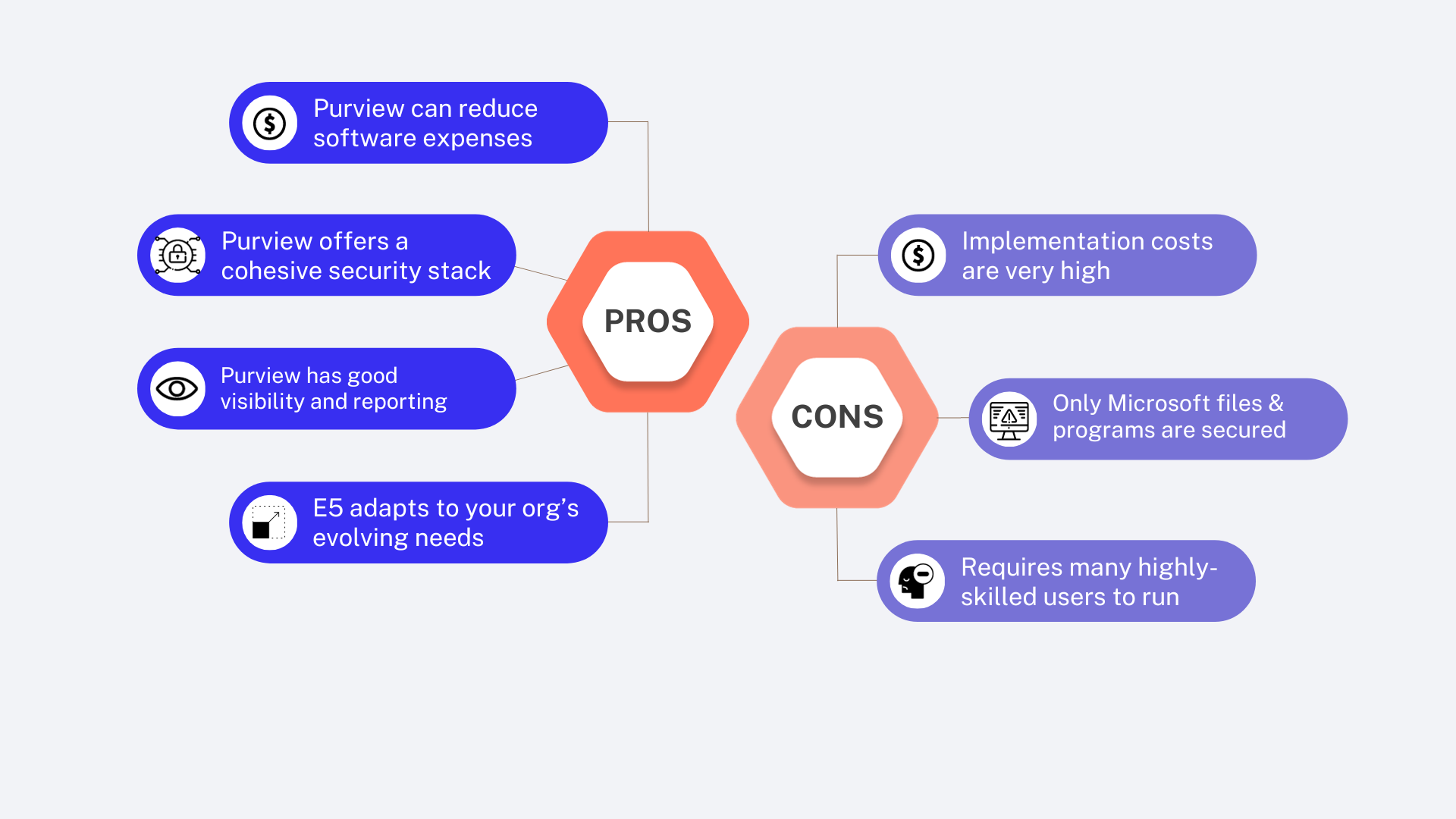
CISOs have been under the microscope for rising security costs. Purview offers opportunities to tackle these challenges:
In summary, Purview could potentially address security cost concerns and offer a scalable approach to improve your cybersecurity posture.
Sounds great, right?
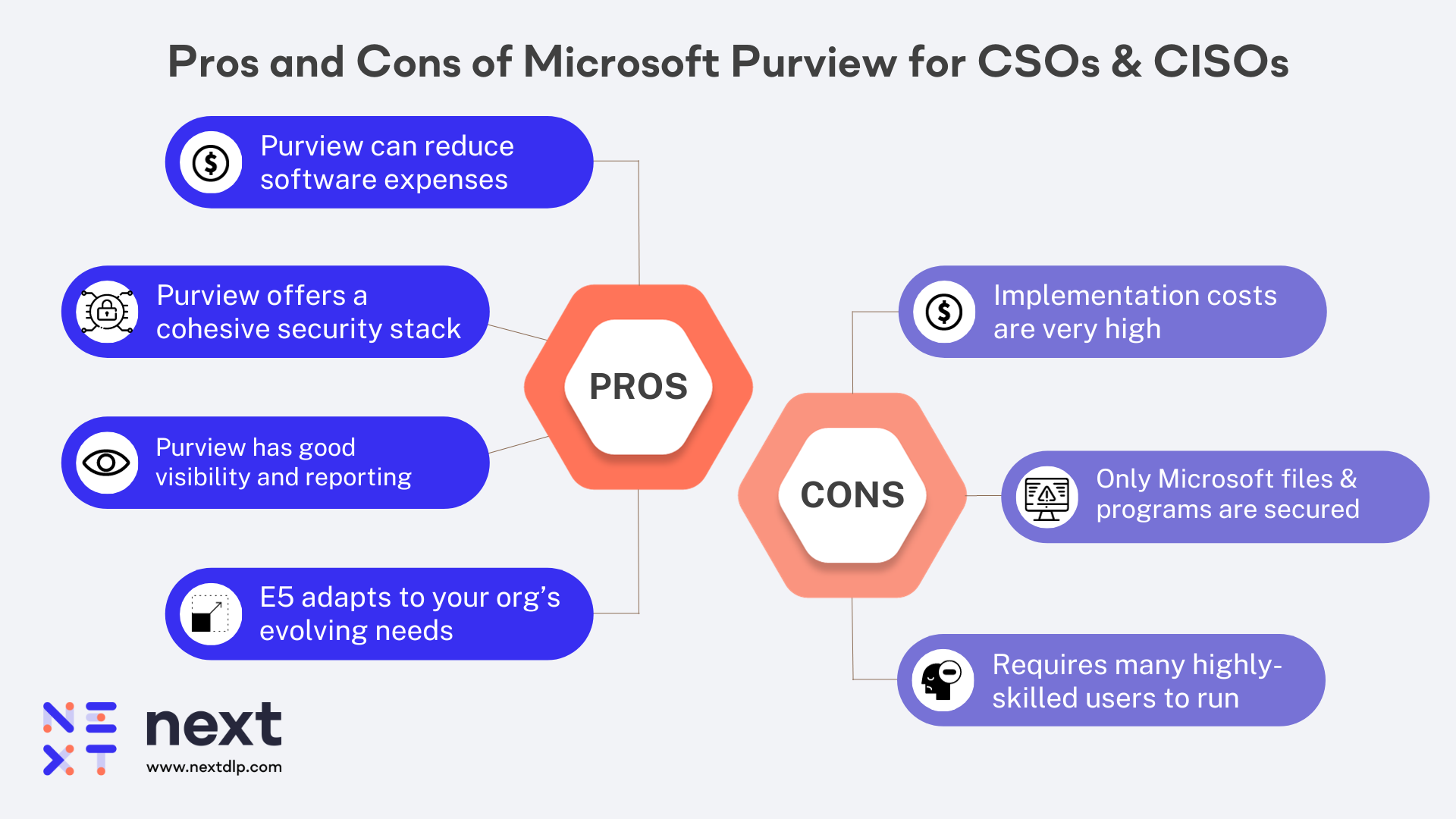
A well-respected industry analyst told me, “If all your data is in O365, then Microsoft will allow you to check that box. If it’s not, you need a different solution.” Leveraging Microsoft Purview requires your business to be all-in on Microsoft as components of the data loss prevention and insider risk solution lean on the capabilities enabled in others (i.e., Microsoft Defender for Endpoint). So CISOs need to think about the following:
Once the true Purview operational costs are added up, how does the security bundle proposition that caught finance’s attention look?
So, you have Purview and need to use it. Here are some steps to help you maximize your company’s investment.
1. Understand Your License: Thoroughly comprehend the components of your Microsoft E5 license, including features like Purview Data Loss Prevention, Microsoft Defender for Endpoint and Purview Insider Risk Management. What do you have? What requires additional investment?
2. Evaluate Your Current Stack: Assess your current security tools and identify your organization's must-have security requirements. Compare these with the features offered by the E5 license and Purview to identify overlaps or gaps.
3. Identify Opportunities: Consider which tools can be replaced by Purview, which should stay as-is, and identify which tools need to be brought in to supplement Purview and improve your security posture. You should be seeking a balance between optimal security coverage and cost efficiency.
4. Define Your Security Outcomes: Develop a roadmap tailored to your specific security goals, such as enhanced data protection, flagging risky behavior, and tracking, tracing and controlling data. Factor in the cost and time of the transition from existing security tools.
So you have Purview but have identified some of the gaps. How do you build the business case for a specialized insider risk and data protection platform? Consider the Reveal Platform by Next DLP, a powerful enhancement to Microsoft Purview. The Reveal Platform and Next DLP enhance Microsoft Purview in 5 key ways:
Let me ask you, “What organization has only Microsoft applications, native Microsoft file types, and nothing else?” That would mean no CAD, no PKG, no PSD, no Apache, no Slack, no Salesforce, no Pages, and no source code. I don’t think such an organization exists. In an era where data security and privacy are paramount, Reveal offers a comprehensive suite of features that safeguard your data, regardless of location. It supports a wide array of data types, seamlessly integrates with third-party and SaaS applications, and accommodates data stored in cloud, hybrid cloud, and on-premises environments without requiring expensive discovery and classification projects.
Purview does well with table-stakes data protection use cases and scenarios: for example, a user attempting to send email via Outlook while connected to the network or blocking patient info from being shared in a Teams channel. Reveal takes DLP and IRM to the next level, utilizing Machine Learning on endpoints to establish a baseline "normal" data behavior and swiftly identifying deviations from this norm. Furthermore, Reveal ensures secure data flow by tracking, tracing, and, when necessary, controlling data movement within your ecosystem, guaranteeing robust protection.
We all know that subpar data classification undermines DLP policies and that misconfigured policies can impede business users from getting their work done. This is one of the reasons why DLP has such a bad reputation. Microsoft DLP requires discovery, labeling and classification to enable successful policy creation. As mentioned earlier, customers need to go all-in on Microsoft, which creates a dependence on Azure Information Protection (f.k.a. MIP) as the sole source of determining sensitivity. Labeling and classifying can take years, leading to accuracy issues. Finally, once that policy is written, unfortunately, it is not shared across the rest of the Purview collection.
As Reveal doesn’t require discovery or classification, it provides immediate visibility into data movement and real-time inspection. Reveal customers derive value from the platform within the first week.
As Purview is a collection of applications, customers report needing five or six different consoles and a significant investment in training its people to run it. Visibility into all sensitive data events requires multiple applications, agents, and consoles. The alerts must then be manually aggregated and reviewed or sent to another solution, e.g., Power BI, for analysis. We all know that DLP alerts can be noisy and difficult to act on. When the time to respond is essential, every added step, process, or tool contributes to alert fatigue, reduces effectiveness, and increases risk.
What sets Reveal apart is its ability to provide instant value and insights, all without the need for complex policies. It offers a unified console view that gives you complete and contextual visibility into IRM and DLP events, empowering you with the knowledge you need to make informed decisions regarding your sensitive data. Reveal consolidates all IRM and DLP events, giving analysts the insights to see “who did what with what data” and the context around the actions.
Anyone who has ever dealt with Microsoft Support knows how difficult it is to work with them to resolve issues or implement new features. With an innovative and agile R&D team at its core and a commitment to delivering world-class customer experiences, Next DLP takes your satisfaction seriously. In fact, 96.8% of Next DLP customers have expressed high satisfaction in surveys, with a remarkable net retention rate of 134%. This demonstrates not only the effectiveness of the Reveal Platform but also the growing trust and expansion of its user base.
Beyond built-in capabilities, Reveal’s API integrations with Splunk, MIP, LDAP, and SaaS apps and alignment with MITRE ATT&CK framework and MITRE Insider Threat knowledge base significantly strengthens a security ecosystem's detection and response capabilities.
Maximizing the value of your Microsoft E5 license and Purview requires a strategic, well-informed approach. It involves more than adopting new technology or embracing an aggressively discounted license that finance teams adore; it's about reshaping your security strategy, leveraging Microsoft's capabilities, quantifying the total cost of ownership, understanding your gaps, and aligning them with your organization's goals and security needs.
A Microsoft security stack has many advantages, but organizations should ensure it’s the best fit before committing. Evaluate:
Implementing Purview has plenty of upsides, but organizations need to plan for its challenges to ensure long-term success. Plan for adequate staffing and training and consider the complexity of deployment. You may also want to engage external experts or consultants to assist with the implementation and ongoing management of Purview.
Purview is a robust solution, but more is often needed to guard against data loss and breaches. Look into specialized data protection and insider risk management solutions like the Reveal Platform by Next, which offers enhanced features and support for a broader range of data types and applications.
Implemented effectively, Purview can reduce costs, improve security scalability, and improve visibility across your IT infrastructure. Teams using Purview also frequently report a more cohesive, all-in-one security solution.
Purview has many advantages, but implementation isn’t always simple. Managers must contend with these obstacles for a successful implementation:

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
